Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)

RE-ENCRYPTION KEY GENERATOR, RE-ENCRYPTION APPARATUS, AND PROGRAM - diagram, schematic, and image 09
File:KG-83 Key Generator Encryption-Decryption Equipment - National Cryptologic Museum - DSC08014.JPG - Wikimedia Commons
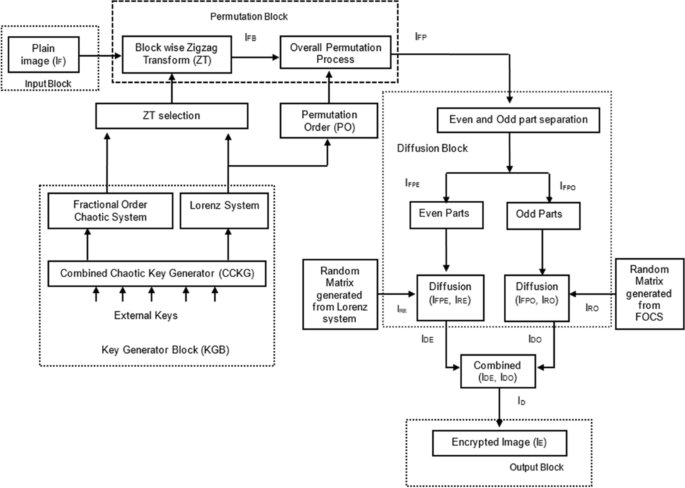
A one-round medical image encryption algorithm based on a combined chaotic key generator | SpringerLink
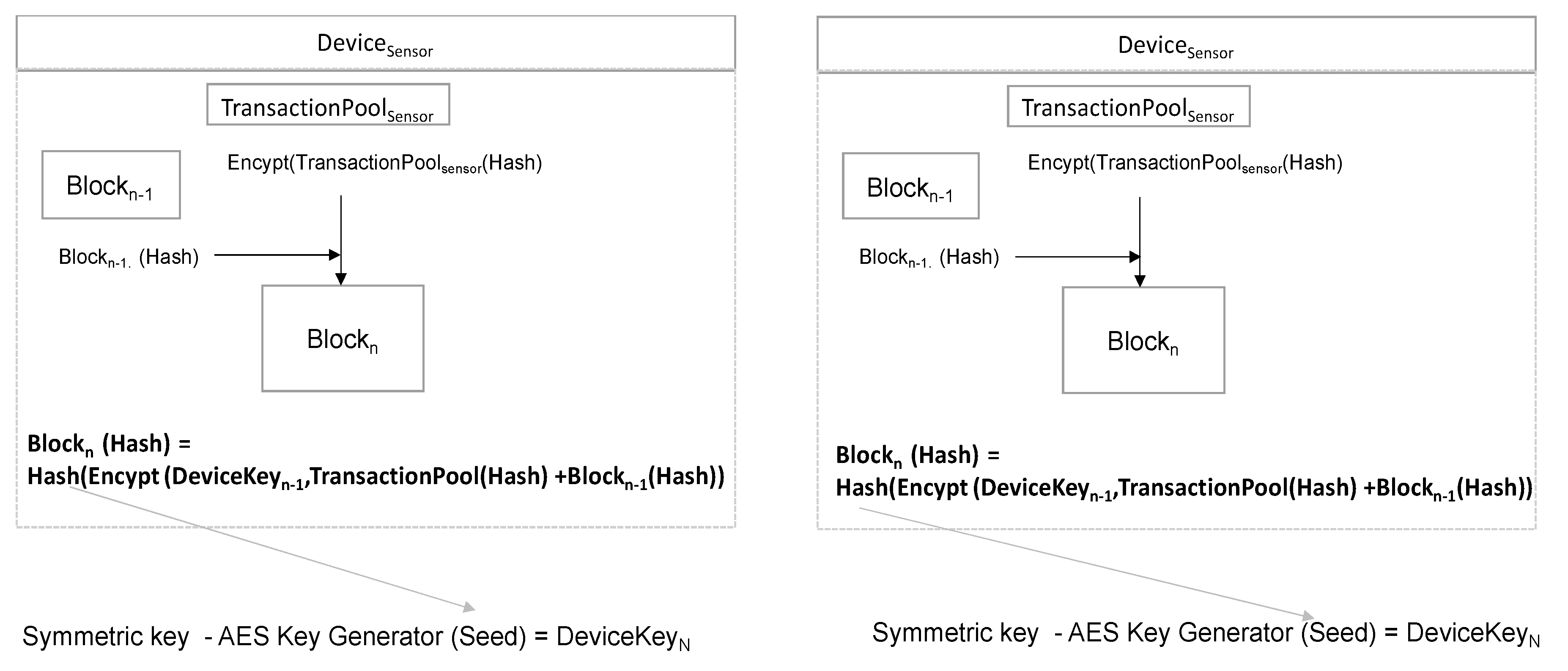
Applied Sciences | Free Full-Text | Block Data Record-Based Dynamic Encryption Key Generation Method for Security between Devices in Low Power Wireless Communication Environment of IoT
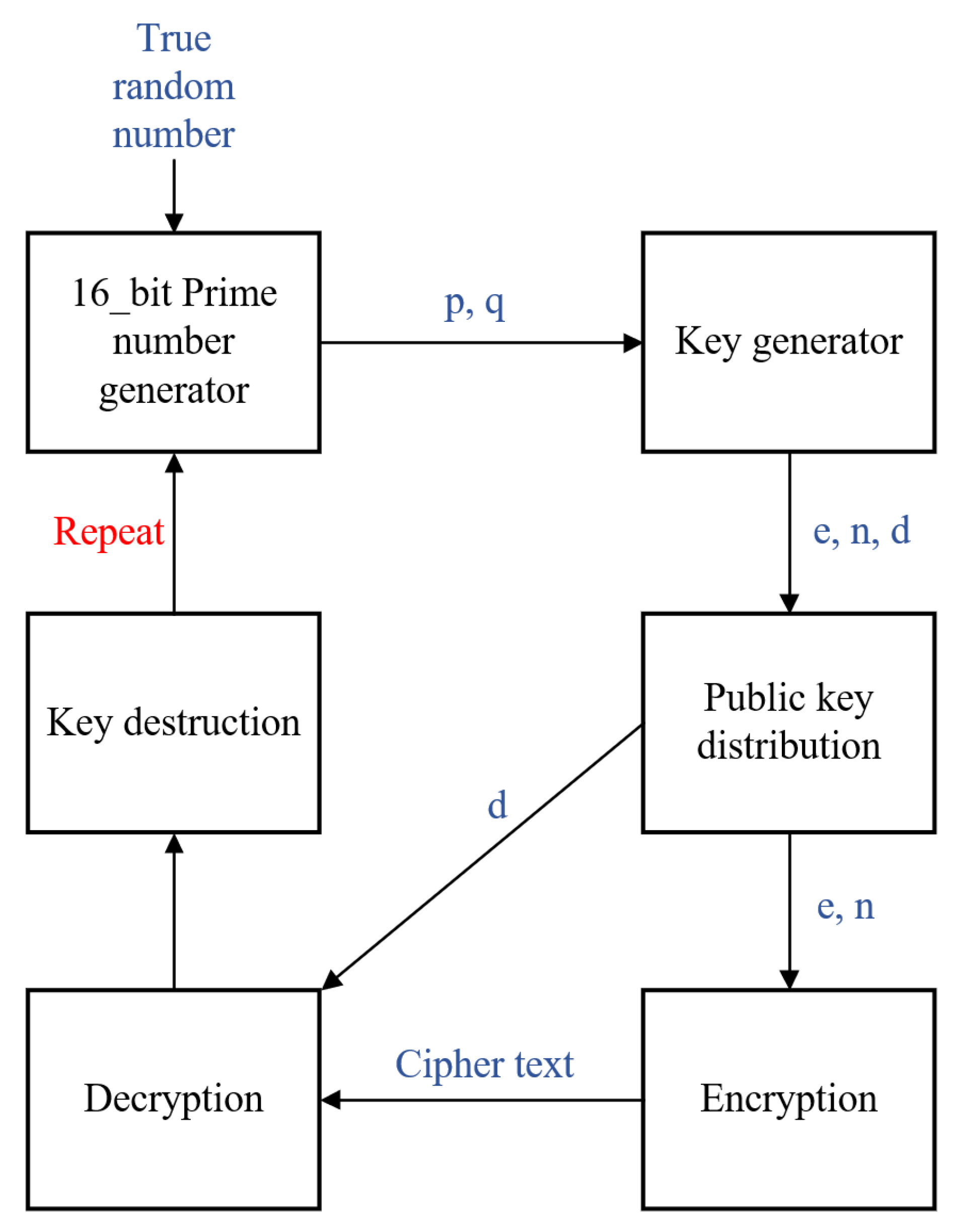
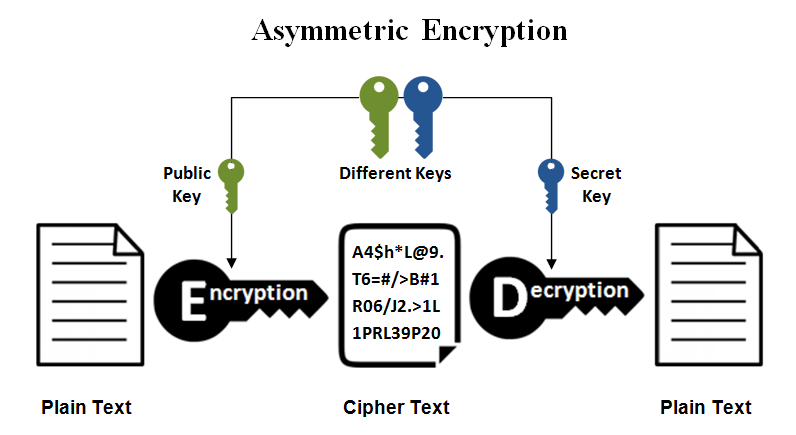
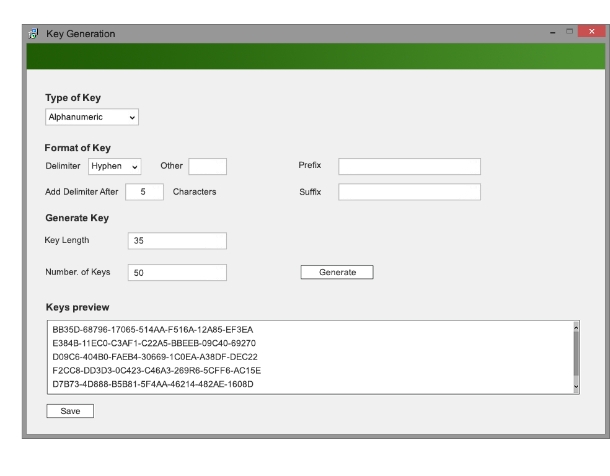
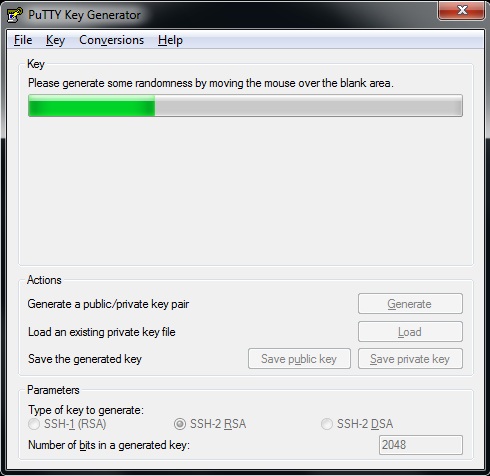
Online RSA Key Generator,Encryption and Decryption web application-Spring Boot web application free download